The global economy faces an existential threat from counterfeiting, a menace that undermines brand equity, endangers consumer safety, and erodes revenue streams across industries. As supply chains become increasingly complex, the limitations of traditional security measures have become glaringly apparent. For enterprise leaders, the conversation is shifting from simple labeling to comprehensive, infrastructure-level security. Consequently, forward-thinking brand protection companies are evolving their strategies, moving away from overt markers like holograms and basic QR codes toward sophisticated, covert cryptographic solutions. This article analyzes the technological shift in the industry, exploring why invisible infrastructure is becoming the standard for authenticating products and securing the global supply chain.
The Escalating Threat Landscape and the Role of Brand Protection Companies
Counterfeiting is no longer a localized issue confined to luxury goods; it has permeated critical sectors including pharmaceuticals, automotive, and agriculture. The sophistication of counterfeiters has evolved in lockstep with technology, enabling them to replicate visible security features with alarming accuracy. According to the OECD and EUIPO, the trade in counterfeit goods accounted for up to 3.3% of global trade in 2019, representing a staggering economic drain.
For brand protection companies, the challenge is no longer just about deterring casual copying but about combating organized crime networks equipped with advanced manufacturing capabilities. Enforcement remains difficult without robust authentication mechanisms at the product level. The most effective brand protection companies are those that acknowledge that visible authentication is merely a speed bump for fraudsters, whereas cryptographic security creates a formidable barrier.
Table 1: The Global Economic Impact of Counterfeiting by Sector
Industry Sector | Estimated Trade in Fakes (Annual) | Primary Risk Vector |
|---|---|---|
Electronics | > $100 Billion | Component diversion & safety failures |
Pharmaceuticals | > $70 Billion | Patient safety & regulatory non-compliance |
Automotive | > $40 Billion | Unsafe parts & warranty fraud |
FMCG / Apparel | > $90 Billion | Brand dilution & revenue loss |
Industrial / Agro | > $30 Billion | Equipment failure & crop damage |
The Critical Failure of Overt Authentication Strategies
For decades, the industry standard relied on overt anti-counterfeit technology: holograms, color-shifting ink, and specialized packaging. While these features offer a degree of visual tamper evidence, they suffer from a fatal flaw. Once a counterfeiter reverse-engineers the visual marker which they inevitably do—they can reproduce it at scale. Furthermore, overt features often require special training or consumer education to be effective, leading to inconsistent brand authentication in the field.
Similarly, the reliance on serialized barcodes and QR codes presents security vulnerabilities. While useful for logistics and track-and-trace, standard barcodes are easily cloned. If a code is copied from a genuine product and applied to a counterfeit one, the system validates the fake as authentic. This limitation highlights a crucial distinction between tracking a product's location and verifying its intrinsic authenticity. Modern brand protection companies must solve the problem of "clone-proof" security, ensuring that the verification mechanism is tied directly to the product's physical existence in a way that cannot be copied.
Table 2: Comparative Analysis of Authentication Technologies
Feature | Overt (Holograms/Labels) | Digital/Track & Trace (QR/RFID) | Covert Cryptographic (Invisible) |
|---|---|---|---|
Visibility to Counterfeiters | High (Easy to copy) | High (Easily cloned) | None (Impossible to copy) |
Impact on Packaging Design | Intrusive (Adds elements) | Moderate (Requires space) | Zero Impact (Invisible) |
Verification Hardware | Naked eye or specialized scanner | Smartphone/RFID reader | Standard Smartphone |
Supply Chain Integration | Low (Physical security only) | Medium (Data logging) | High (Real-time verification + data) |
Long-term Durability | Low (Labels can be removed) | Medium (Can be damaged) | High (Embedded in substrate) |
The Evolution to Invisible Cryptographic Infrastructure
The future of packaging security lies in invisibility. By embedding cryptographic signatures directly into the product or its packaging via existing printing processes, companies can create a "digital twin" of every item without altering its visual appearance. This approach, often referred to as covert or invisible brand protection, utilizes the random variations inherent in manufacturing or applies microscopic patterns undetectable to the human eye.
This invisible infrastructure transforms the product itself into a unique security key. Unlike a label that can be peeled off or a hologram that can be copied, the cryptographic signature is intrinsic to the item. This technology leverages smart packaging principles, where the physical container communicates securely with digital systems. Because the markers are invisible, counterfeiters have no target to replicate. They cannot steal what they cannot see.
For enterprise leaders, this represents a paradigm shift. The role of brand protection companies transitions from providing security stickers to providing a layer of invisible, trust-enabled infrastructure. This infrastructure utilizes anti-counterfeit technology that is interoperable with existing manufacturing lines, requiring no new hardware or slowdowns in production. The result is a seamless integration of security into the product lifecycle, from the factory floor to the end consumer.
How Covert Technology Outperforms Traditional Track-and-Trace
While track-and-trace systems are essential for supply chain visibility, they are not sufficient for standalone product verification. Track-and-trace answers the question, "Where has this box been?" It does not inherently answer, "Is this box genuine?" Covert cryptographic solutions bridge this gap.
When a product is protected with invisible signatures, verification can be performed anywhere using a standard smartphone. The device's camera captures the invisible signature, and cloud-based cryptographic services validate it against the secure ledger in real-time. This process, often called mobile verification, empowers everyone in the ecosystem warehouse workers, customs officers, retailers, and consumers—to act as authenticators.
This capability creates a real-time defense network. If a counterfeit is detected, the system can geotag the location, providing brand protection companies and their clients with actionable intelligence to intercept fraudulent goods. This moves the strategy from reactive investigation to proactive interdiction. It is the difference between discovering a cache of fake goods months after they have entered the market and stopping them at the point of inspection.
Operationalizing Invisible Infrastructure: The Verification Workflow
Implementing invisible infrastructure does not require overhauling manufacturing processes. The technology is designed to be non-disruptive. In a typical deployment, the covert signatures are applied during the standard printing phase of packaging. This requires no special inks, RFID tags, or additional hardware. The "magic" happens in the digital realm and the smartphone application.
Figure 1: The Covert Verification Lifecycle
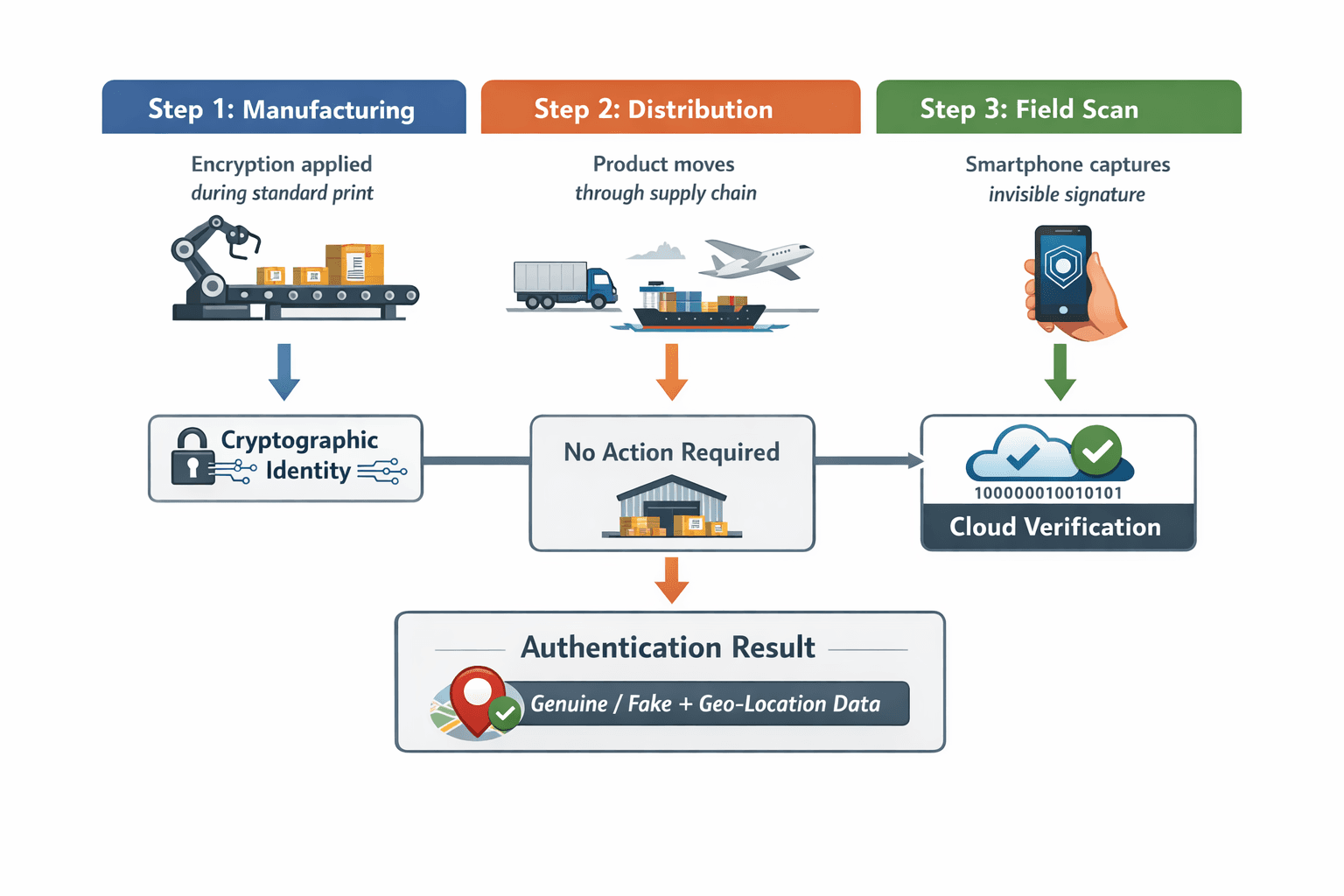
This operational model ensures that digital brand protection is scalable across millions of units. Because the verification is tied to the smartphone ecosystem, it leverages the ubiquity of mobile devices to create a massive, decentralized verification network. This is particularly powerful for industries with complex distribution chains, such as the automotive aftermarket, where counterfeit parts can pose significant safety risks.
Sector-Specific Applications and Strategic Outcomes
The application of covert cryptographic infrastructure varies by industry, but the core value proposition remains the same: irrefutable proof of authenticity.
Pharmaceuticals and Healthcare: Patient safety is paramount. Covert authentication supports compliance with regulations like the DSCSA, ensuring that pharmaceuticals and healthcare products are genuine. Unlike overt labels that might be stigmatized, invisible markers preserve the integrity of the medical packaging while providing pharmacists and patients with instant product verification. Data suggests that authentication technologies can reduce the cost of investigations by up to 60% in high-risk pharmaceutical markets.
Automotive: The automotive industry is plagued by counterfeit parts that range from low-quality filters to critical safety components. Invisible signatures allow manufacturers and mechanics to verify parts without accessing proprietary databases or scanning visible QR codes that might be damaged. This secures the automotive aftermarket and protects brand trust.
FMCG and Consumer Goods: In the fast-moving consumer goods sector, speed is critical. Overt checks slow down the supply chain. Invisible verification allows for rapid authentication at distribution centers. Furthermore, it protects brand loyalty by ensuring consumers receive authentic products, a crucial factor for FMCG and consumer goods brands.
Luxury Goods: For high-value items, aesthetics cannot be compromised. Invisible brand authentication allows luxury houses to protect their goods without defacing them with ugly holograms or tags, maintaining the premium feel while securing the brand against sophisticated fakes.
Key Criteria for Selecting Brand Protection Companies
As enterprise leaders evaluate potential security partners, the criteria must extend beyond cost. The selection of a partner is a strategic decision that impacts long-term brand resilience. When assessing brand protection companies, consider the following technical and operational metrics:
Cryptographic Provenance: Does the solution rely on standard encryption standards or proprietary, unvetted algorithms? True security requires mathematically sound cryptographic foundations.
Scalability and Integration: Can the solution scale to billions of units without latency? Does it integrate easily with existing ERP and WMS systems?
Non-Disruptive Implementation: Does the technology require changes to the packaging line, such as new inks or labels? The best solutions work with existing printing processes.
Frictionless Verification: Can the product be verified with a standard smartphone without specialized hardware? High friction leads to low adoption in the field.
ROI and Economic Impact: A robust solution should demonstrate a clear return on investment by recovering revenue and reducing investigative costs. Utilizing tools like an ROI calculator can help quantify these benefits before deployment.
Table 3: Vendor Selection Scorecard
Evaluation Criterion | Weight | Legacy Vendor (Overt) | Modern Infrastructure Vendor (Covert) |
|---|---|---|---|
Clone-Resistance | High | Low (Visuals can be copied) | High (Crypto-based) |
Supply Chain Disruption | Medium | High (New consumables needed) | Low (Software-centric) |
Consumer Engagement | Medium | High (Visible interaction) | Medium-High (App-based) |
Data Intelligence | High | Low (Manual checks) | Real-time automated analytics |
Implementation Cost | High | Low-Medium | Medium (High long-term ROI) |
An Enterprise Adoption Roadmap for Anti-Counterfeit Technology
Adopting invisible cryptographic infrastructure is a phased process. Successful brand protection companies advocate for a strategic roadmap rather than a "big bang" deployment.
Discovery and Risk Assessment: Identify high-value product lines (SKUs) most vulnerable to counterfeiting. Analyze the supply chain chokepoints where verification is most critical.
Pilot Program: Deploy the technology on a limited production run. Validate the ease of integration with printing partners and test the user experience of the mobile verification app.
Integration: Connect the verification platform with enterprise systems. This allows for the automated logging of authentication events, creating a rich dataset for supply chain visibility.
Scale and Rollout: Expand the solution to other SKUs and geographic regions. Train field teams and customs officials on how to use the verification tools.
Governance and Response: Establish protocols for acting on counterfeit alerts. The value of the system is realized only when the organization acts on the intelligence provided.
This roadmap ensures that the adoption of anti-counterfeit technology aligns with business objectives and operational capabilities.
Conclusion
The era of relying on visible labels and holograms as the primary defense against counterfeiting is drawing to a close. As counterfeiters become more sophisticated, enterprise leaders must adopt more advanced, covert measures. The modern standard for security is invisible infrastructure—cryptographic signatures that provide irrefutable proof of authenticity without disrupting the manufacturing process or the consumer experience.
By partnering with innovative brand protection companies, enterprises can transform their supply chains from vulnerable pipelines into secure, verifiable ecosystems. This shift not only recovers lost revenue but also strengthens the vital bond of trust between brands and their customers. In an age of uncertainty, the ability to verify a product’s identity instantly and definitely is not just a competitive advantage; it is a necessity for survival.



