The Integrity Imperative: A Strategic Mandate for the C-Suite
Executive Summary: The Illusion of Security
Most Fortune 500 executive teams are operating under a dangerous delusion. They believe that because they have a Brand Protection department, a Legal team, and a budget for takedowns, their brand is "protected." In reality, they are funding a high-priced game of "whack-a-mole" that manages symptoms while the underlying disease systemic illicit trade erodes the enterprise's core value.
This guide is not a manual for operational enforcement. It is a strategic reframing of brand protection as a fiduciary responsibility and a critical enterprise risk. We will challenge the comfortable assumptions that have led to the current state of "managed failure" and introduce a framework for evolving toward true enterprise resilience.
Part I: The C-Suite Blind Spot
The Enforcement Trap: Motion Without Progress
The most common failure in brand protection is the Enforcement Trap. This occurs when success is measured by activity rather than impact. Executives are often presented with impressive-looking dashboards showing thousands of URL takedowns, millions of dollars in "seized goods value," and dozens of successful raids.
However, these metrics are often meaningless. If you take down 10,000 listings but the illicit market share of your product remains constant or grows, you haven't protected the brand; you've merely paid a "takedown tax" to stay in the game. The Enforcement Trap creates a false sense of security, allowing the C-suite to check a box while the brand's revenue integrity continues to bleed out.
The reality is that the illicit market is an agile, highly efficient competitor. While your Legal team is drafting a cease-and-desist letter, the counterfeiter has already moved their operation to a new domain, a new marketplace, or a new jurisdiction. Your "motion" is their "operating cost," and they are far better at managing their costs than you are at managing your defenses.
The Silo Fallacy: A Governance Failure
Brand protection is typically siloed within Legal or Security. This is a fundamental governance error. Counterfeiting is a cross-functional business threat that impacts every facet of the enterprise:
• Supply Chain: Through diversion, gray market activity, and the infiltration of fake components.
• Marketing: By eroding brand premium and confusing customer experiences.
• Finance: Through direct revenue loss and the long-term degradation of brand equity.
• Quality/R&D: By undermining the value of innovation and exposing the company to product liability.
When brand protection is siloed, it lacks the authority and the visibility to address the root causes of vulnerability. It becomes a reactive "clean-up crew" rather than a proactive strategic partner. The C-suite must recognize that brand integrity is not a "legal problem" to be solved; it is a business condition to be managed.
Part II: The Brand Integrity Maturity Framework (BIMF)
To move beyond the Enforcement Trap, organizations must evolve. We have developed the Brand Integrity Maturity Framework (BIMF) to help C-level leaders assess their current state and chart a path toward resilience.
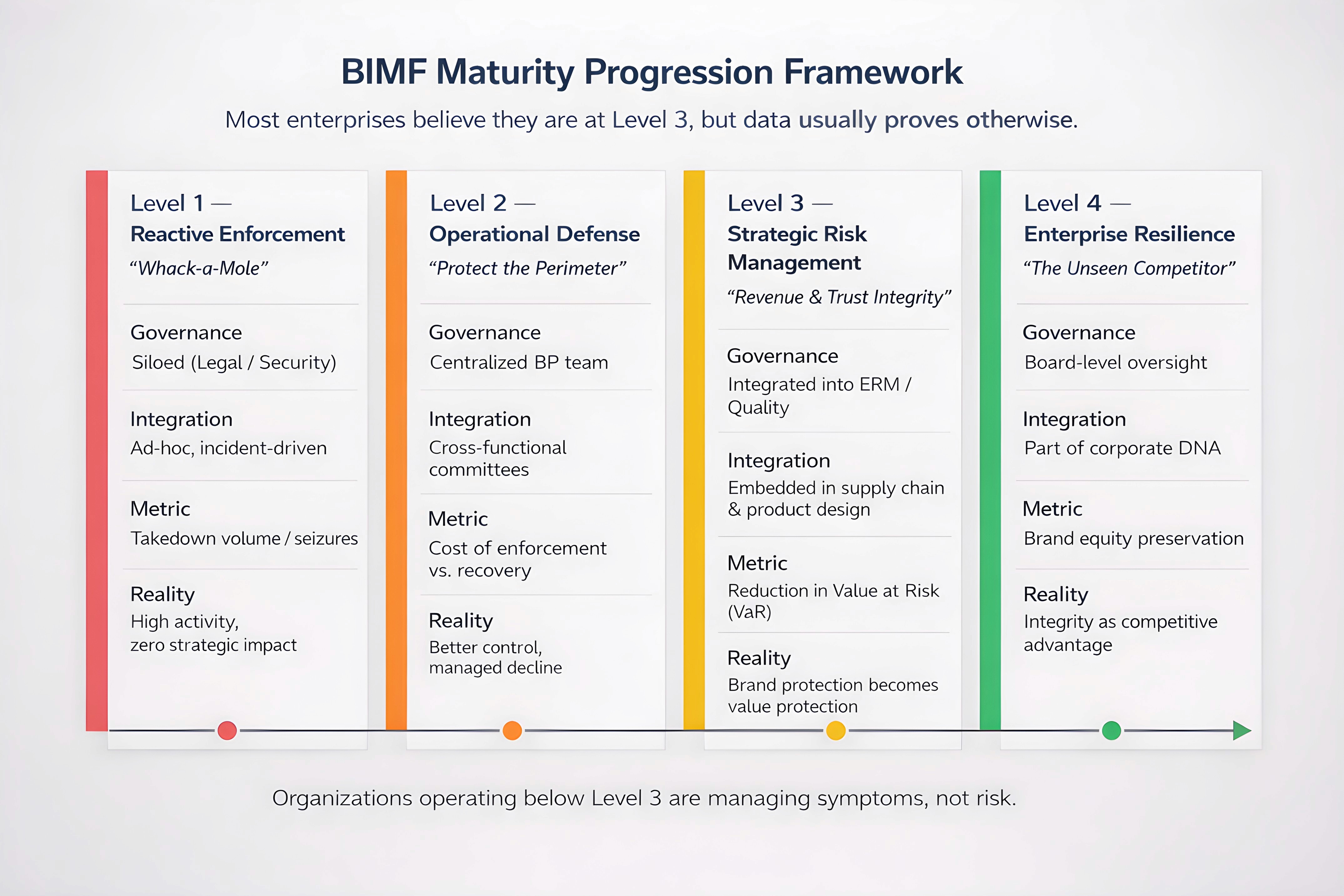
Maturity Level | Mindset | Governance | Integration | Key Metric |
Level 1: Reactive Enforcement | "Whack-a-mole" | Siloed (Legal/Security) | Ad-, event-driven | Number of takedowns/seizures |
Level 2: Operational Defense | "Protect the Perimeter" | Centralized BP Team | Cross-functional committees | Cost of enforcement vs. recovery |
Level 3: Strategic Risk Management | "Revenue & Trust Integrity" | Integrated into ERM / Quality | Embedded in supply chain & product dev | Reduction in Value at Risk (VaR) |
Level 4: Enterprise Resilience | "The Unseen Competitor" | Board-level Oversight | Part of the Corporate DNA / Culture | Brand Equity Preservation |
Level 1: Reactive Enforcement (The Status Quo)
At this level, the organization reacts to "fires." A major counterfeit incident is discovered, a raid is conducted, and the legal team files a lawsuit. There is no overarching strategy, and the goal is damage control. Most companies at this level are losing significant market share without even knowing it. They are "blind" to the true scale of the problem.
Level 2: Operational Defense (The "Managed Failure" State)
This is where most Fortune 500 companies reside. They have a dedicated Brand Protection team and use external vendors for monitoring. They have cross-functional committees that meet quarterly. While more organized, they are still trapped in the cycle of managing symptoms. They measure success by the volume of their own activity. They are "managing the decline" rather than stopping it.
Level 3: Strategic Risk Management (The Turning Point)
At Level 3, the organization recognizes brand protection as an Enterprise Risk Management (ERM) issue. Brand integrity is integrated into the Quality and Supply Chain functions. The focus shifts from "how many fakes did we find?" to "how much revenue did we protect?" Metrics are aligned with business outcomes, and the program is viewed as a value-protector. This is where the organization begins to "win."
Level 4: Enterprise Resilience (The Competitive Advantage)
At the highest level of maturity, brand integrity is part of the corporate culture. The Board of Directors has direct oversight, and the organization treats the counterfeiter as an Unseen Competitor. Every employee, from R&D to Sales, understands their role in protecting the brand's integrity. At this level, brand protection is not a cost; it is a source of competitive advantage and customer trust. The brand is "hardened" against attack.
BIMF Self-Assessment Scorecard: Where Does Your Organization Stand?
To initiate the transition, the Board must first establish an honest baseline. Use this scorecard to assess your organization's current maturity level. If the majority of your answers fall into a single column, that is your current BIMF level.
Question | Level 1: Reactive Enforcement | Level 2: Operational Defense | Level 3: Strategic Risk Management | Level 4: Enterprise Resilience |
1. Primary Metric | Takedown Volume / Seizures | Cost of Enforcement vs. Recovery | Reduction in Value at Risk (VaR) | Brand Equity Preservation |
2. Governance | Siloed (Legal/Security) | Centralized BP Team | Integrated into ERM / Quality | Board-level Oversight |
3. Product Design | No involvement | Post-production review | "Integrity by Design" Mandate | Zero-Trust Authentication |
4. Supply Chain | Ad-hoc audits | Contractual compliance | Forensic monitoring / Data Analytics | Material Tagging / Digital Twins |
5. Technology | Manual monitoring / Legacy vendors | Automated takedown tools | AI-driven detection / Predictive analytics | Invisible Authentication / Blockchain |
6. Executive Accountability | None | Budget approval | VaR-based performance metrics | Bonuses tied to Brand Equity |
Part III: The "Uncomfortable" Reality of Executive Liability
This is the section that most C-level leaders prefer to ignore. The failure to protect brand integrity is not just a business loss; it is a potential legal and personal liability.
Contributory and Vicarious Liability: The End of "Plausible Deniability"
Courts are increasingly looking at whether companies have taken "reasonable steps" to prevent their brands from being used in illicit trade. If your product is being counterfeited and causing harm whether it's a fake pharmaceutical, a defective auto part, or a hazardous toy the "I didn't know" defense is rapidly losing its power.
Executives can be held liable for Contributory Infringement if it can be shown that the company facilitated the illicit trade through negligence or a lack of oversight. Furthermore, the doctrine of Vicarious Liability can hold the enterprise responsible for the actions of its third-party partners and distributors if they are found to be complicit in diversion or counterfeiting. In the eyes of the law, your "blind spot" is your "negligence."
The Fiduciary Failure: A Breach of Trust
As a C-level leader, you have a fiduciary duty to protect the assets of the corporation. The brand is often the most valuable asset on the balance sheet. If you are funding a brand protection program that you know (or should know) is ineffective, you are failing in your fiduciary duty. This exposure is not just to regulators, but to shareholder activists who are increasingly using brand erosion as a lever for leadership change. A failure in brand integrity is a failure in leadership.
Part IV: Decision-Making Principles (The Strategic Mandate)
The following principles are designed to be uncomfortable. They require a fundamental shift in how you lead and how you allocate resources.
1. Stop Funding "Noise": Demand Impact, Not Activity
If your Brand Protection team presents you with a report full of "takedown numbers," ask them one question: "What was the impact on our illicit market share?" If they can't answer, stop the funding. You are paying for motion, not progress. Demand that every dollar spent on brand protection be tied to a measurable reduction in Value at Risk (VaR). If you can't measure the impact, you aren't managing the risk.
2. Mandate "Integrity by Design": Stop Building Vulnerable Products
Brand protection should not be a "bolt-on" at the end of the manufacturing process. It must be integrated into the R&D and Product Development phase. If your products are easy to counterfeit, that is a design failure. Mandate that every new product includes "integrity features" whether physical, digital, or forensic that make it prohibitively expensive for the "Unseen Competitor" to copy. If you aren't building integrity into the product, you are building vulnerability into the brand.
3. Weaponize Your Supply Chain: Eliminate the "Blind Spots"
Your supply chain is either your greatest vulnerability or your strongest defense. Most companies have "blind spots" in their distribution networks where diversion and gray market activity thrive. Mandate a Zero-Trust Supply Chain policy. Use data analytics to identify anomalies in ordering patterns and hold your distributors and partners contractually (and financially) responsible for any leakage. Your partners should fear your audit more than they value the counterfeiter's kickback.
4. Elevate the "Unseen Competitor": Know Your Enemy
Instruct your strategy team to conduct a Competitive Analysis of the illicit market. Who are the "CEOs" of the counterfeit networks? What is their "R&D" strategy? How do they manage their "logistics"? By treating the counterfeiter as a legitimate (albeit illicit) competitor, you move from a defensive, legalistic mindset to a proactive, strategic one. If you don't understand their business model, you can't disrupt it.
Part V: The Future Risk Landscape: The AI and Decentralization Threat
The threat to brand integrity is evolving faster than your current defenses.
AI-Driven Counterfeiting: The End of Manual Enforcement
The advent of Generative AI has fundamentally altered the economics of counterfeiting. In the past, creating a convincing replica of a premium brand's packaging or marketing collateral required significant investment in design and printing technology. Today, the "Unseen Competitor" uses AI to generate pixel-perfect replicas of your brand's visual identity in seconds. To understand the full scope of this threat, review the Anti-Counterfeiting Technology Trends 2025 report. This is not just about aesthetics; AI is being used to reverse-engineer digital authentication features, simulate secure QR codes, and even generate synthetic voices for fraudulent customer support interactions.
Furthermore, AI-driven automation allows counterfeiters to operate at a scale that renders manual enforcement obsolete. A single illicit actor can deploy thousands of AI-managed storefronts across hundreds of global marketplaces, each with unique, AI-generated product descriptions and customer reviews. When one storefront is taken down, the system automatically generates ten more to replace it. This is the "Hydra Effect" of AI-driven illicit trade. To survive in this environment, your brand protection strategy must move beyond human-led monitoring. You must fight AI with AI deploying automated, machine-learning-driven detection and response systems that can identify and neutralize threats at the speed of the algorithm. If your defense is human-speed and your attacker is AI-speed, you have already lost.
Decentralized Marketplaces: The "Dark Web" Goes Mainstream
The rise of decentralized, peer-to-peer (P2P) marketplaces and the integration of blockchain technology into illicit trade networks present a profound challenge to traditional brand protection. In a centralized marketplace like Amazon or eBay, there is a "choke point" a central authority that can be served with legal notices and held accountable for infringing activity. In a decentralized environment, there is no central server, no corporate entity, and no "off" switch.
The "Unseen Competitor" is increasingly leveraging these decentralized platforms to conduct business with total anonymity. Transactions are settled in privacy-focused cryptocurrencies, and logistics are managed through fragmented, "last-mile" delivery networks that bypass traditional customs checkpoints. Protecting your brand in this environment requires a fundamental shift from enforcement to authentication. You can no longer rely on "stopping the fakes" at the source; instead, you must empower your customers with foolproof, decentralized verification tools that allow them to verify the "source of truth" for your products directly on the blockchain. The future of brand protection is not in the courtroom; it is in the code.
The Geopolitical Risk of Illicit Trade
For the C-suite of a global enterprise, brand protection is also a geopolitical issue. Counterfeiting and illicit trade are frequently linked to transnational organized crime, extremist groups, and even state-sponsored economic warfare. When your brand's integrity is compromised, you are not just losing revenue; you may be unwittingly funding activities that undermine global stability and expose your organization to severe reputational and regulatory risks under international sanctions and anti-money laundering (AML) laws.
The "Unseen Competitor" often operates in jurisdictions where intellectual property enforcement is deprioritized or used as a tool of industrial policy. In these environments, your legal remedies are limited, and your traditional enforcement strategies may even be counterproductive. Navigating this landscape requires a sophisticated understanding of geopolitical risk and a brand protection strategy that is integrated with your organization's broader government relations and corporate social responsibility (CSR) mandates. Brand integrity is a pillar of corporate diplomacy.
Part VI: The Technology of Resilience: The Zero-Trust Enabler
The mandate for "Integrity by Design" (Part IV) requires a technology that is both invisible to the counterfeiter and non-disruptive to the supply chain. Traditional overt technologies holograms, QR codes, visible security threads fail this test because they are easily copied, reverse-engineered, or removed. They are a "bolt-on" that adds cost without adding resilience.
The only viable mechanism for achieving Level 4 Enterprise Resilience is Invisible Authentication.
Technology Type | Counterfeiter Vulnerability | Supply Chain Disruption | BIMF Level Supported |
Overt (Holograms, Visible Codes) | High (Easily copied or removed) | Low (Simple application) | Level 1-2 (Reactive/Operational) |
Covert (UV Ink, Microtext) | Medium (Requires specialized equipment to detect) | Medium (Requires specialized application) | Level 2-3 (Operational/Strategic) |
Invisible Authentication (Digital Fingerprints, Material Signatures) | Extremely Low (Non-disruptive, embedded in the product/packaging) | Minimal (Integrated into existing processes) | Level 4 (Enterprise Resilience) |
Invisible Authentication (e.g., digital fingerprints, material signatures) is the Zero-Trust Enabler for brand integrity. It works by embedding a unique, non-disruptive signature into the product or packaging that is invisible to the naked eye and requires proprietary anti-counterfeiting technology to read.
Zero-Trust Supply Chain: Because the signature is non-disruptive and can be applied at the material or component level, it allows for forensic monitoring of the supply chain without slowing down production. Every unit's journey can be tracked, eliminating the "Ghost Shift" and providing irrefutable evidence of leakage.
Zero-Trust Customer Experience: It allows customers to verify authenticity instantly via a simple, non-invasive scan, shifting the burden of proof from the brand to the product itself. This is the ultimate defense against AI-driven visual counterfeiting.
This technology is the bridge from abstract strategy to concrete, measurable resilience.
Part VII: The Cost of Inaction (CoI) vs. ROI
Executives often ask for the ROI of brand protection. This is the wrong question. The right question is: "What is the Cost of Inaction?"
The "Trust Tax": The increased cost of customer acquisition as trust in your brand erodes.
The "Liability Premium": The increased cost of insurance and legal defense as counterfeit-related incidents rise.
The "Equity Discount": The reduction in your company's valuation as investors price in the risk of brand erosion.
If you don't invest in brand integrity, you are effectively paying a "failure tax" that is far higher than the cost of a proactive program.
The Back-of-the-Napkin Liability Audit: Estimating Value at Risk (VaR)
To provide the Board with a tangible, immediate estimate of the financial risk, use this heuristic to calculate a conservative Value at Risk (VaR) figure. This is not a replacement for a full audit, but a necessary tool to force the conversation.
$$
\text{VaR} = (\text{Estimated Illicit Market Share} \times \text{Annual Revenue}) + (\text{Brand Equity Value} \times \text{Erosion Factor}) + \text{Contingent Liability}
$$
Variable | Definition | Heuristic/Source |
Estimated Illicit Market Share | The percentage of your product category sold illicitly. | Use a conservative estimate (e.g., 5% to 10%) from industry reports or internal intelligence. |
Annual Revenue | Your company's total annual revenue. | From your latest financial report. |
Brand Equity Value | The intangible value of your brand. | Use a conservative figure, such as 10% of your company's market capitalization. |
Erosion Factor | The percentage of brand equity at risk from a major integrity failure. | Use a conservative estimate (e.g., 1% to 5%). |
Contingent Liability | Estimated cost of a single major product liability lawsuit. | Use the average settlement/judgment cost for a major product recall in your industry (e.g., $50M - $500M). |
The Mandate: Present this calculation to the Board. The resulting number is the minimum financial exposure you are currently tolerating by remaining in the Enforcement Trap.
Part VIII: Case Studies in Managed Failure and Strategic Resilience Threat" and Supply Chain Leakage
One of the most uncomfortable truths for C-level executives is that a significant portion of brand integrity failures originate from within their own ecosystem. This is not just about disgruntled employees; it is about the systemic leakage that occurs when authorized manufacturers, distributors, and logistics partners engage in "over-runs" or "side-door" sales.
Research indicates that up to 85% of trade secret thefts and a substantial percentage of high-quality counterfeits are facilitated by individuals or entities with legitimate access to the brand's IP (Wilson, 2021). This is the "Ghost Shift" phenomenon, where an authorized factory runs a third shift using the same molds, materials, and designs to produce "authentic fakes" for the illicit market.
To address this, the C-suite must move beyond simple audits and implement forensic supply chain monitoring. This involves:
• Material Tagging: Using microscopic or chemical markers in raw materials to verify the origin of every component.
• Digital Twins: Creating a digital record for every unit produced, allowing for real-time verification of authorized production volumes.
• Incentive Alignment: Restructuring contracts to reward partners for integrity and penalize them severely for leakage, moving from a transactional relationship to a strategic partnership.
The "Gray Market" as a Gateway Drug
Gray market activity the unauthorized sale of genuine products outside of intended channels is often viewed as a minor nuisance or even a "safety valve" for excess inventory. This is a strategic error. The gray market is the primary infrastructure through which counterfeiters "salt" the market with fakes.
When you allow your products to be sold through unauthorized channels, you are training your customers to look for "deals" outside of your control. This creates the perfect environment for the "Unseen Competitor" to insert their fakes into the stream of commerce. A brand that cannot control its distribution cannot protect its integrity.
Part VIII: Case Studies in Managed Failure and Strategic Resilience
Case Study 1: The "Whack-a-Mole" Trap in Consumer Electronics
A global consumer electronics brand invested over $50 million annually in a brand protection program focused on online takedowns and physical raids. Their dashboards showed a 95% success rate in removing infringing listings. However, an independent audit revealed that their illicit market share had actually increased by 12% over the same period.
The failure was rooted in the "Enforcement Trap." The brand was targeting low-level resellers while the primary counterfeit networks were simply rotating their digital infrastructure. By the time a listing was taken down, three more had appeared. The brand eventually shifted to a Level 3 BIMF approach, integrating authentication technology into their firmware and weaponizing their supply chain data to identify the source of the leakage. Within 18 months, their illicit market share dropped by 40%, and their authorized sales grew by 15%.
Case Study 2: The "Integrity by Design" Success in Pharmaceuticals
A major pharmaceutical company faced a crisis when counterfeit versions of a life-saving medication were found in several emerging markets. Instead of relying solely on legal enforcement, the CEO mandated an "Integrity by Design" initiative.
The company redesigned the packaging to include multiple layers of overt and covert security features, including a unique digital identifier for every bottle that customers could verify via a mobile app. They also implemented a "Zero-Trust" policy for their distributors, requiring real-time reporting of inventory movements. This holistic approach not only eliminated the fakes from the market but also significantly increased customer trust and brand loyalty in those regions.
Part IX: The Board-Level Mandate: A Fiduciary Checklist
As a C-level leader, your oversight of brand integrity should be as rigorous as your oversight of financial reporting. Use the following checklist to evaluate your organization's readiness:
1 Governance and Accountability: Does the head of Brand Protection have a direct reporting line to the C-suite (COO, CQO, or CEO), or is the function buried three layers deep in the Legal department? Is brand integrity a recurring, high-priority agenda item for the Board's Risk and Audit Committees? More importantly, are executive bonuses tied to the reduction of Value at Risk (VaR) and the preservation of brand equity? If there is no financial accountability at the top, there will be no strategic priority at the bottom.
2 Strategic Metrics vs. Vanity Metrics: Are you still being briefed on "takedown volume" and "seizures," or are you demanding data on Illicit Market Share and the Cost of Inaction (CoI)? Do you have a clear understanding of the "Trust Tax" your brand is paying in key markets? If your metrics don't reflect business outcomes, they are vanity metrics designed to mask a lack of progress.
3 Cross-Functional Integration: Is brand integrity a mandatory requirement in the Product Development Lifecycle? Are your R&D and Engineering teams held accountable for the "counterfeit-ability" of their designs? Does your Marketing team understand how gray market activity is eroding your brand premium? If brand protection is seen as "someone else's job," it is nobody's job.
4 Supply Chain Transparency and Forensic Audit: Do you have real-time, granular visibility into your authorized manufacturers' production volumes and material flows? Do you have a "Zero-Trust" policy for third-party distributors that includes unannounced forensic audits and material tagging? If you can't account for every unit produced under your brand name, you are inviting leakage.
5 Technological Readiness: Are you leveraging AI-driven detection, blockchain-based authentication, and forensic material markers, or are you still relying on manual processes and legacy vendors who are incentivized by activity rather than impact? In the fight against the "Unseen Competitor," technology is the ultimate force multiplier.
6 Liability and Fiduciary Risk: Have you conducted a comprehensive Product Liability and Fiduciary Risk Audit to assess your personal and corporate exposure to counterfeit-related harm? Do you have a crisis management plan in place for a catastrophic brand integrity failure? If you aren't prepared for the worst, you are vulnerable to it.
Part X: The 90-Day Turnaround: An Immediate Action Plan
The transition from the Enforcement Trap to Enterprise Resilience requires immediate, decisive action. This 90-day plan is designed to force the necessary organizational and strategic shifts, culminating in a Board-level mandate for the long-term transformation.
Phase | Week | Focus | Deliverable | Strategic Goal |
I. Audit & Exposure | Week 1-4 | Fiduciary Risk Assessment | Board Memo on VaR: Present the "Back-of-the-Napkin Liability Audit" (Part VII) and the BIMF Self-Assessment (Part II) to the Board Risk Committee. | Force the Conversation: Shift the Board's focus from operational cost to fiduciary risk and liability. |
| Week 5-8 | Supply Chain Blind Spot Mapping | Zero-Trust Pilot Plan: Identify the single most vulnerable product line or distributor channel. Map its flow and identify all "blind spots" where the "Ghost Shift" could occur. | Identify the Leakage: Pinpoint the source of the problem, not just the symptoms. |
II. Pilot & Proof | Week 9-12 | Technology of Resilience Pilot | Invisible Authentication PoC: Launch a small-scale Proof of Concept (PoC) using Invisible Authentication technology on the vulnerable product line identified in Week 8. | Prove the Viability: Demonstrate that Level 4 resilience is achievable without disrupting production. |
III. Mandate & Scale | Week 13 | Executive Mandate | The Integrity Imperative Report: Present the PoC results, the updated VaR, and the full strategic plan to the Executive Committee. | Secure the Budget: Gain executive approval for the multi-year, cross-functional transition to BIMF Level 3/4. |
Part XI: Conclusion: The Leadership Imperative
The integrity of your brand is the ultimate measure of your leadership. In an era of radical transparency and systemic risk, you can no longer hide behind the "operational periphery" of brand protection. The "Unseen Competitor" is not just stealing your revenue; they are stealing your future.
The transition from Managed Failure to Enterprise Resilience is not a project; it is a cultural transformation. It requires the courage to challenge comfortable assumptions, the discipline to mandate cross-functional integration, and the vision to treat brand integrity as a source of competitive advantage.
The choice is yours: Lead the transition, or manage the decline. The "Unseen Competitor" is already making their move. What is yours?
References
• Anatomy of Product Liability: Causes and Consequences (Finch McCranie)
◦ https://www.finchmccranie.com/blog/anatomy-of-product-liability-causes-and-consequences/
• Reduce Your Liability Exposure and Costs associated with Counterfeit and Knockoff Products (Frost Brown Todd)
• Contributory and Vicarious Liability in Trademark Infringement (Mintz)
• The Economic Impacts of Counterfeiting and Piracy (INTA / Frontier Economics)
• The High Cost of Executives' Intellectual Property Blind Spots (Sloan Review)
◦ https://sloanreview.mit.edu/article/the-high-cost-of-executives-intellectual-property-blind-spots/
• Hands Off My Brand! The Financial Consequences of Protecting Brands Through Trademark Infringement Lawsuits (Sage Journals)
◦ https://journals.sagepub.com/doi/10.1509/jm.17.0328
• Organizing for brand protection and responding to product counterfeit risk: An analysis of global firms (Springer)
◦ https://link.springer.com/article/10.1057/bm.2016.12
• The Future of Brand Protection: Responding to the Global Risk (Springer)
◦ https://link.springer.com/article/10.1057/s41262-017-0032-x
• Changing Executive Mindsets on Global Product Integrity (NC State)
• A Strategic Roadmap for Building Brand Protection Programs (Wilson, 2021)
◦ https://jeremywilson.org/wp-content/uploads/2021/04/Brand-ProtectionRoadmap_WP_Final.pdf
• Trademark Counterfeiting and Individual Purchaser Liability (National Law Review)
◦ https://natlawreview.com/article/trademark-counterfeiting-and-individual-purchaser-liability

